U-PROX CLC G80
Standalone control panel

identifiers
for configuration

Сontrol panel for one door
touch button
events


Standalone control panel
Access control panel for one door
Standalone control panel
- Programming via smartphone
- Easy installation
- Supports U-PROX readers
- 500 cards and 1000 events
- Designed for maximum autonomy


Single-sided door control panel
- Single-sided door
- Built-in RTE (REX) touch button
- DC, RTE (REX) inputs
- Solid state relay for the lock control
- Alarm output
Advanced operating modes
- Day and night schedules
- Auto learning
- Mode “Free pass by card”
- Mode “access to the ATM”

Gallery
Photos and videos
NEW PRODUCTS
Want to buy?
Contact partner companies to purchase or install security and automation devices.
Want to sell?
Become an official distributor, reseller or installer of U-PROX security and safety systems.
TECHNICAL SPECIFICATIONS
| Inputs |
DC - Door Contact RTE - Request to Exit button Built-in RTE touch button |
|---|---|
| Outputs (Relays) |
NO, COM - solid state relay, 1 A @ 30 V (inversion relay mode) OUT - alarm output, OC 0.16 A @ 12 V (inversion relay mode) |
| Reader | RS232: one reader U-PROX SE/SL, up to 10 m |
| Memory |
508 user ID’s 1000 events "Day" and "Night" modes |
| Power | +10,8...+15 V, consumption < 70 mA @12V |
| Dimensions | 84.3 х 84.3 х 14.5 mm |
| Weight | 0.15 kg |
| Case colour | black |
| Case material | ABS+PC plastic, Gorilla Glass |
| Operating temperature range | from 0°C to +50°C |
| Configuration | With the U-PROX Config mobile app via Bluetooth |
| Complete set |
1. U-Prox CLC G80; 2. Mounting kit; 3. Quick start guide |








U-PROX CLC G80 User manual
Description
The U-PROX CLC G80 control panel is an autonomous device designed to control access in residential and industrial premises.
The control panel is supplied in a case with a built-in “request-to-exit” touch button, without a power supply unit.
The control panel operates with one reader connected via an RS-232 interface (supported U-PROX readers only) and one actuating device. The control panel processes information received from the reader via an RS232 interface and, using an integrated relay, switches the actuating device (for example, an electric lock).
The control panel has two inputs with fixed functions — a door sensor and a request-to-exit button.
The control panel can operate autonomously. It allows for setting access rules, editing the list of identifiers, and complete configuration of the control panel with U-PROX Config via Bluetooth Low Energy (BLE).
Device Purpose
The U-PROX CLC G80 control panel is designed for autonomous operation and to organize access control to one entry point.
Technical Specifications
- Autonomous mode
- Supply Voltage: +10.8 … +15 V
- Current Consumption from a 12V Source: not more than 70 mA
- Supply Ripple Amplitude: not more than 500 mV
- Connection of one U-PROX contactless identifier reader
- Built-in touch exit request button
- Door contact input (DC)
- Input for connecting the built-in exit request button (RTE)
- Tamper contact for control case opening
- One relay (NO, NC, COM): 3 A @ 12 V
- Alarm transistor output (open collector): 12 V, 160 mA
- Configuration via smartphone using Bluetooth (BLE)
- Real-time clock and non-volatile memory:
- Identifiers – 508
- Events – 1000
- “Day” and “Night” modes. Works on schedule and/or manually
- Overall dimensions: 84.3 × 84.3 × 14.5 mm
- Case material and color: ABS+PC, Gorilla Glass, black
- Weight: 0.15 kg
- Climatic version: IP42 (from 0 to +50°C); operational at relative humidity up to 80% without condensation
Terms
Identifiers: Each user in access control systems has a unique code. Identifiers can be in the form of plastic cards, key fobs, mobile devices, etc.
Reader: Devices for reading codes that connect to the control panel. Only U-PROX series readers can be connected to the U-PROX CLC G80.
Keypad Code: A keypad code can be entered using a reader with an integrated keypad.
Doors: The access control point (e.g., door, turnstile, access booth). The access point is the logical unit of the access control system.
Exit Request Button: Used for exiting the premises; other methods of opening may trigger a “DOOR TAMPER” event.
Door Contact: Input for connecting sensors (magnetic, rotary, limit switch) to monitor the door status.
“Door Time” Interval: The period during which, after a user is granted access, the door is not monitored even if the contact is interrupted.
Identifier attempt detection: If several unregistered identifiers are presented consecutively, the control panel switches to alarm mode.
Loading: After programming, the settings are loaded into the controller.
Description
Controller Structure
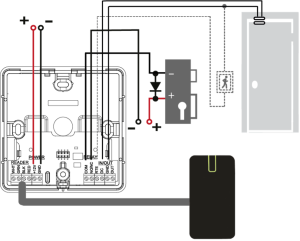
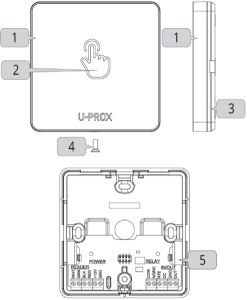
The control panel consists of the following components:
 |
|
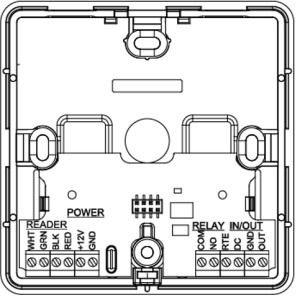
Control panel Terminal Functions
The layout of the connectors on the bottom board of the device is shown in Fig. 2.
| Contact | Name | Purpose |
|---|---|---|
| GND | – | External power supply connection V- |
| +12V | – | External power supply connection V- |
| NO/NC | Normal open/Normal closed | Relay contacts |
| COM | Common | Relay contacts |
| RED | +12V | ReaderV+ |
| BLK | GND | ReaderV- |
| GRN | Data 0 | Reader Data Rx |
| WHT | Data 1 | Reader Data Tx |
| GND | – | Ground |
| DC | Door Contact | – |
| RTE | Request to Exit Button | – |
| OUT | Alarm Output | – |
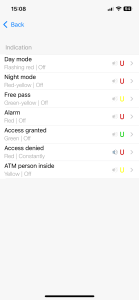
Control panel Indication
Access modes are indicated by the reader connected to the control panel. The default settings are as follows:
- Standby Mode: no sound, reader LED blinks red once per second
- Night Mode or Lockout: no sound, red-yellow blinking once per second
- Alarm: no sound, solid red
- Card Registration: no sound, green LED blinks once per second
- Initialization: no sound, no light indication
- Data Reading/Loading, Firmware Update: no sound, continuously blue
- Access Granted: short beep, steady green; 5 seconds before the door time expires – a short beep once per second
- Access Denied: continuous beep, solid red
The touch button LED indicates button pressing only!
Controller Operation
Control panels are shipped in an unconfigured (factory) state. In this state, the controller’s red LED blinks once per second.
To operate the control panel, it must be configured using the configuration software on a mobile device. After the settings are loaded, the control panel enters the “Standby” mode.
Control panel Operating Modes
The control panel can operate in the following modes:
- Day Mode
- Night Mode
- Programming Mode
- Code Selection Block Mode
In the day mode, the reader’s LED blinks red. When a registered identifier is presented, the programmed action is executed (usually – relay activation). In night mode, only identifiers with 24/7 access are active. Mode switching is done by presenting a special identifier or automatically according to a schedule.
In any mode, when a duress code is entered, the control panel immediately triggers the alarm output.
Code Entry or Proximity Card Presentation
Code entry is performed by sequentially pressing the keys on the reader’s keypad. The code length must be between 4 and 10 digits, and the entry is terminated by pressing [#]. Each key press is accompanied by a short buzzer sound. Correct entry is confirmed by a short beep, an error by a long beep.
After several incorrect or unregistered code entries, the reader will lock for 40 seconds. To cancel the entry, press [*]. If no key is pressed within 40 seconds, the entered data is erased and the device returns to its current mode.
Presenting a proximity card (at a distance of a few centimeters) is equivalent to code entry. The type of identifier is determined by the reader.
Using the U-PROX Mobile ID app for identification from mobile devices (via Bluetooth Low Energy) is equivalent to code entry or card presentation.
Time Parameters
Default Time: For convenient configuration, default time intervals are provided in the control panel. For example, a relay time value of 255 means the factory setting of 3 seconds. If several codes are set to a relay time of 255, it indicates the “default relay time”. Changing this value affects the parameters of all codes with this setting.
Entry/Exit Time: After the relay is activated, a delay for entry/exit begins. If the door remains open 5 seconds before the delay ends, a warning beep is activated. The value can range from 0 to 253 seconds.
“Open Door” Mode: If the entry/exit time for a certain code is set to 254 seconds, after presenting this code, door status monitoring stops until the door is closed again.
Code Guessing Block: If an unregistered identifier is presented three times in a row, the control panel enters a blocking mode for a specified time.
Controller Programming
- Download and install the U-PROX Config software (hereinafter – the configurator).
|
Supported devices: Android 5.0 and above, and Apple devices with iOS 8.0 and above, that have Bluetooth 4.0 and above with BLE support. |
- Launch U-PROX Config
- Tap the “Search” button to begin searching for devices.
If Bluetooth is not enabled, the app will prompt you to enable it; tap “OK”.
|
Attention! For BLE technology location services must be enabled. |
- Select the control panel from the device list and tap the “Connect” button – an engineer code prompt will be displayed.
- After entering the correct code, the control panel configuration will be displayed.
If an attempt is made to connect without authorization, a message will appear in the app window indicating that access is not permitted.
- After reading the configuration, the main menu becomes available. Advanced functions will be displayed after selecting the “NEXT” option.

If changes have been made to the configuration, the “Write to Device” menu option becomes available. After tapping it, the configuration will be written to the control panel’s memory.
To disconnect from the control panel, tap the “Disconnect” (X) button.
|
Attention! If you disconnect without writing the configuration, all changes will be lost. |
After forming and loading the configuration, the device is ready for operation.
Settings Menu
This menu contains the main settings of the control panel.
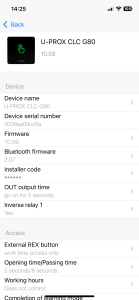
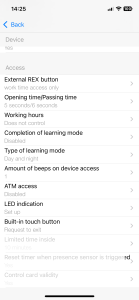
Device Settings Group
- “Device Name” – change the control panel’s name
- “Device Serial Number” – unique identifier of control panel
- “Firmware Version” and “Bluetooth Version” – view versions and update the firmware
- “Installer Code” – change the engineer code (a new code is accepted if it does not match existing user codes or duress codes)
- “OUT Output” – the time for activating the alarm output OUT (from 0 to 240 seconds)
- “Inverse Relay” – switch between relay operating modes (NO and NC)
Access Settings Group
- “External REX (RTE) Button” – configuration of the operating modes for the RTE input (input for exit request button):
- “work time access only” – the button operates only on day schedule interval
- “24/7” – the button operates 24/7
- “24/7 + toggles day-night” – the button operates 24/7 and used for manually switching the “day/night” schedule
- “Opening time/Passing time” – set the default relay activation time (from 2 to 254 seconds) and door passage waiting time.
- “Working Hours” – configure automatic mode change: within the specified time interval the device operates in day mode, outside the interval in night mode; if disabled, switching is possible only manually via the corresponding identifier or REX button.
- One minute before switching to night mode, the control panel emits a short beep once per second, and 20 seconds before – two short beeps per second
- “Number of Sound Signals on Access” – set the sound indication for granted access (0, 1 or 5 signals)
- “LED indication” – configure custom indication in various control panels modes
- “Built-in touch Button” – enable/disable the built-in touch button
Learning Mode
This mode is used for automatically memorizing identifiers when they are presented to the reader (for example, when replacing the control panel or if user cards have not yet been added). When learning mode is enabled, the control panel automatically grants access, unlocks the relay, and stores the identifier in memory. The learning mode operates under limitations regarding time and the number of supported identifiers.
To enable Learning mode enable “Completion of Learning mode” section and set date and time of completion.
“Type of Learning Mode” – indicates the access level under which identifiers will be stored during learning (for example, “Day and Night” or “Day”).
ATM Mode
This mode is used for organizing access to premises for users with certain types of identifiers. In this mode, identifiers are not stored in the control panel’s memory – decisions are made based on the reader’s input. Additionally, a function for monitoring the duration of stay in the premises is available. For this purpose, a motion sensor is connected to the RTE input with an installed resistor.
The mode settings include:
- “ATM Mode” – enable or disable the mode
- “Limited Stay Time” – set the maximum allowed time in the premises; if exceeded, the control panel’s OUT output is activated
- “Reset Timer on Motion” – if enabled, the timer resets when the motion sensor is triggered
- “Control Card Validity” – enable or disable control over the expiration of the identifier (requires additional reader configuration)
Access Menu
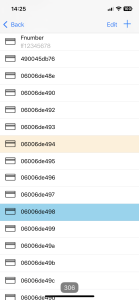
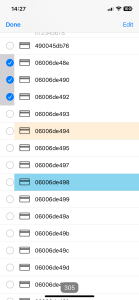
The main “Access” menu contains a list of codes loaded into the control panel.
Each list item includes:
- An identifier with an indication of the access type (Day – white background; 24/7 – orange; No access – gray; Free passage mode – light blue)
- The user name or numeric value of code if no name is provided
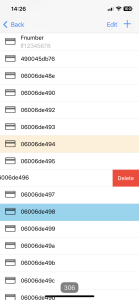
Identifier Deletion
To delete an identifier, swipe the item from right to left and press “Delete” button. The item will be marked as deleted. To cancel deletion, tap “Cancel”.
Identifier Addition
To register a new card, present it to the reader connected to the control panel – the card will be added to the list with default settings.
To register a keyboard code, enter it via the reader, ending with [#] – the code will be added to the list with default settings.
To register a mobile identifier, present the mobile device with the U-PROX Mobile ID app (with U-PROX BLE ID) to the reader (at a distance of 5–10 cm) and tap the “Open” button in the app – will be added to the list with default settings.
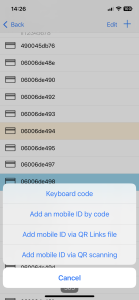
To manually enter a keyboard code in the app, tap the “Add” (+) button, select “keyboard code” and enter it.
To manually add a mobile identifier by code, tap the “Add” (+) button, select “Add an mobile ID by code” and enter the code printed below the QR code.
To add mobile identifiers from a QR Links file, tap the “Add” (+) button, select “Add mobile ID via QR Links file”, choose the desired file and tap “Upload”.
To add mobile identifiers using QR scanning, tap the “Add” (+) button, select “Add mobile ID via QRscanning” and scan the QR codes using a smartphone with the U-PROX Config app.
Identifier Parameter Settings
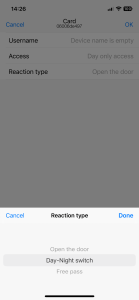
To change the access parameters for an identifier, select it from the list (tap the item). A parameter window will open where you can configure:
- Name
- Access category (“Day only” or “24/7”)
- Type of reaction to identifier presentation
To save the changes, tap the “OK” button. To edit parameters for multiple identifiers, press “Edit” button and select items in the list. Change the parameters and save by tapping “OK”.
To exit the “Access” section, tap the “Back” button.
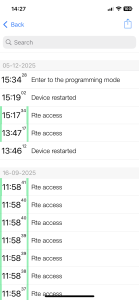
Journal Menu
This menu allows you to view the event history, filter events, and export the journal for further analysis.
To export the journal, tap the corresponding button – the journal will be saved in the device’s temporary memory. The U-PROX Config app will offer options to save or send the journal using built-in methods.
To exit the “Journal” section, tap the “Back” button.
Update Menu
This menu allows you to update the control panel’s firmware via BLE. After selecting this option, the app will prompt you to choose an update from cloud storage or local storage – a list of *.bin files will be displayed, and the update will start upon file selection.
After selecting the “From local storage” option, a list of available *.bin files will be displayed. Select one – the firmware update process will begin.
Attention! All local firmware files must be located in the “Download” folder (Android) or local storage of application (iPhone).
Device Configuration Backup and Restore
Select the “Template” menu option. A menu with actions will appear: “Save” and “Restore”.
When selecting “Save”, all settings are recorded to a file with the *.eep extension on the mobile device.
When selecting “Restore”, a list of available configuration files will be displayed, from which you can choose the desired file to load the settings into the control panel.
Mobile Identifier
Download and install the U-PROX Mobile ID app. Devices running Android 5.0 and above with Bluetooth 4.0 (BLE) are supported. Launch the app and add an identifier via QR code or U-PROX Desktop.
Present the mobile device to the reader (10–20 cm away) and tap the “Open” button – data exchange will occur. If the identifier is registered and has the correct rights, access will be granted and the door will open.
Attention! For BLE to work on Android 6.0 and above, location services must be enabled.
How to work with the device
The control panel is housed in a compact plastic case. Its connection and installation are performed according to the following instructions.
Installation Procedure
At the installation site, perform the following steps:
- Mark the location and drill the required holes.
- Screw in the mounting screw located at the bottom of the control panel.
- Remove the top cover.
- Using the back plate as a template, drill two holes with a diameter of 5 mm and a depth of 30 mm.
- Run cables from the power supply unit, actuating device (e.g., electric lock), reader, and control panel inputs to the harnesses.
- Connect the wires according to the following sections (it is recommended to use a junction box).
- Conceal the installation cables in the wall.
- Reattach and secure the back plate, connect the connector for the harness, put on the top cover, and secure it with the screw.
- Complete the full configuration of the control panel using the mobile app.
- The device is ready for operation.
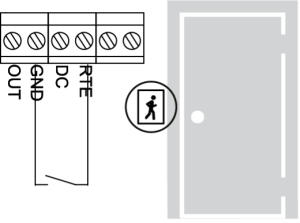
Door Sensor
The control panel determines the door status (open/closed) using the door contact. Without the contact, the control panel cannot detect unauthorized access or a situation where the door remains open for too long.
It is recommended to equip doors controlled by the access system with a door closer.
Attention!!! If you are not using a door contact, the DC input must be shorted between the DC and GND contacts.
Exit Request Button
The door is opened by pressing and releasing the exit request button. Additionally, this button can be used for remote door opening (e.g., by a receptionist or security guard). Using the button on an electric strike triggers a “DOOR BREAK-IN” event.
Actuating Devices (Relay)
To control actuating devices, the control panel is equipped with one solid-state relay. It can be used to control an electric lock or strike. The relay has normally open (NO) contacts and inversion mode (to NC), which allow control of actuating mechanisms with a current consumption of up to 1 A at 30 V.
If all actuating devices are switched on/off simultaneously, voltage drops may occur; these should not cause the control panel to malfunction. If necessary, connect a separate power supply for the actuating devices.
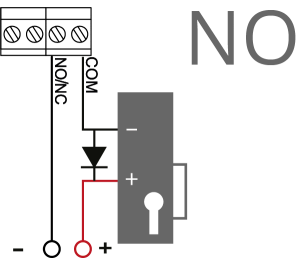
When using the relay contacts to control an inductive load (e.g., an electromagnetic lock), a flyback diode should be installed in reverse across the coil power supply to avoid contact damage.
Low-cost electromagnetic strikes do not support prolonged voltage application. For them, program the relay time accordingly to prevent coil overheating.
Alarm Output
The control panel’s alarm output is transistor-based (open collector). When the OUT contact is activated, it is connected to the GND contact. The alarm output can be used to connect to an external alarm system or an actuating device, provided its current consumption does not exceed 60 mA.
If a door contact (normally closed) is connected to the device harness, the alarm output is activated upon contact opening, except during the entry/exit time interval. The alarm output remains active for a programmed time interval – from 0 to 254 seconds. A value of 0 seconds means the alarm output is not activated, while 255 seconds means it remains active until the alarm is cancelled with the appropriate code or card.
Maintenance
Factory Reset
- Disconnect power from the control panel
- Remove the top cover
- Short-circuit the OUT and DC contacts
- Reattach the top cover
- Apply power and wait 40 seconds
- Disconnect power, remove the top cover, and disconnect the OUT and DC contacts
Engineer Password Reset
- Disconnect power from the control panel
- Remove the top cover
- Short-circuit the OUT and RTE contacts
- Reattach the top cover
- Apply power and wait 40 seconds
- Disconnect power, remove the top cover, and disconnect the OUT and RTE contacts
Factory Settings
- Engineer Code: 1234
- Door Time: 20 seconds; code blocking on multiple incorrect attempts: 40 seconds
- Inputs (loops): RTE – 24/7 mode
- Outputs: Relay – 3 seconds, OUT (alarm) – 10 seconds
Warranty
The manufacturer guarantees that the U-PROX CLC G80 control panel complies with the parameters described in this manual when properly stored and operated.
- Storage warranty period — 6 months from the date of manufacture
- Operational warranty period — 24 months from the date of commissioning
- Delivery, personnel training, installation, commissioning, and warranty service are carried out by the manufacturer or authorized organizations
- In case of a defect caused by the manufacturer, correction is performed within 10 days
- Warranty service is not provided in cases of:
- Incorrect connection,
- Failure to follow this manual,
- Mechanical damage,
- Natural disasters.

Meet the new product that is already available for order - the U-PROX PIR Cam wireless motion detector.
If the detector is triggered, it will send one or a series of photos to assess the situation to the U-PROX Home mobile app and the central monitoring station of the security company. The photo will be sent only during an obvious alarm.
This detector also has the “pet immune” function, which means that it is not sensitive to the movement of animals weighing up to 20 kg and up to 1 m high.
Simple installation, easy addition to the new generation U-PROX MPX security system hub, and an unrivaled communication range with the hub allow you to find a good location in your space.
Clear photo verification of the alarm has the highest quality specifications:
- motion detection range up to 12 m
- photo resolution: 640×480, 320×240, 240×176 pixels
- infrared illumination up to 8 meters for shooting in the dark and low light
- photo transfer time up to 9 seconds.
It should also be noted that U-PROX PIR Cam uses intelligent algorithms to eliminate false alarms. This allows you to be sure that you receive notifications only in case of a real threat.
Choose the new U-PROX PIR Cam with photo verification, because clarity adds peace of mind and comfort to life!

We are very proud to announce our newest achievement - U-PROX SE series readers have successfully passed the SIA OSDP certification, confirming their reliability and security.
SIA (Security Industry Association) experts, recognized authorities in the field, have thoroughly tested and verified the compliance of U-PROX SE series readers with the standard and officially included them in the list of devices that have successfully passed OSDP v2.2 certification.
This is not just a certificate, it is a confirmation of the highest quality and unconditional compliance with the most stringent reliability and security standards in the access control industry.
What is OSDP? It is an advanced communication protocol that guarantees:
- maximum security: data is reliably protected from unauthorized access through encryption and device authentication.
- flawless operation: the access control system functions without failures, providing you with peace of mind and confidence.
- extended functionality: support for more functions than other protocols allows you to use U-PROX SE series readers in systems of any complexity and scale.
- easy integration: easy connection to OSDP-enabled controllers simplifies the process of installing and configuring your system.
From now on U-PROX SE Series readers are an investment in the future, a guarantee of reliable protection and uninterrupted operation of your next-generation access control system.
Завантаження
FAQ
-
- Connect wires D0 (green) and D1 (white) with each other
- Apply power to the reader
- Connect to the reader with application U-Prox Config installed on smartphone.
- Select “Settings”
- Set a password
- Go back
- Press “Save Settings”
- Press “Disconnect”
-
The control panes is the “brain” of the system, which determines whether or not the owner of the identifier is allowed to enter the door.
It has a built-in memory that stores identifier codes with a list of access rights for each of them.
When a person presents (brings to the reader) an identifier, the code read from it is compared with the one stored in the database, on the basis of which a decision is made to open the door.
-
A reader is a device that reads the code (key) of the identifier and transmits it to the controller.
-
PACS — Physical Access Control System —an access control and management system is a set of hardware and software control and management tools.
The main goal is to restrict and register the entry-exit of objects in a given area through “points of passage”: doors, gates, etc.
The main task is to control access to a given territory (who to let in, at what time and to what territory), including also:
- restricting access to a given territory;
- identification of a person who has access to a given territory.
-
An identifier is the basic element of an access control system that stores a code.
Each client is assigned a specific key (code), which serves to determine the owner’s rights – identification.
A card, a key fob, a tag can perform the function of an identifier.
-
Areas of application have a wide range of ACS:
- company offices, business centers;
- banks;
- educational institutions (schools, technical schools, universities);
- industrial enterprises;
- protected areas;
- parking lots;
- places of passage of vehicles;
- private houses;
- residential complexes;
- cottages;
- hotels;
- public institutions (sports complexes, museums, metro, etc.)
-
Everything that is U-PROX, from the idea to the engineering implementation is done exclusively in Ukraine.
-
You can buy U-Prox equipment from our partners.
-
Open formats JSON and SOAP (XML) allow interaction between different applications, exchange data with access control systems and create applications that complement and extend the standard functionality of the U-PROX Web system.
API capabilities:
- Secure data exchange over a computer network.
- WEB service – the opportunity to interact with any platform and programming environment for SOAP and JSON protocols.
- Implementation of the user interface using the API.
- The ability to integrate with other systems and applications implemented by third-party developers.
-
U-PROX WEB provides a full range of solutions for quick installation, configuration and daily use of IP ACS by enterprises of any size, from a small office to a large company with many branches.
U-PROX Web has a full-featured web interface with fine-tuning of all ACS capabilities and provides the ability to monitor events, configure equipment, manage personnel access, and generate reports.